The article, in the biology and neurology categorizations of Nautilus, a very carefully calculated and high quality science website featuring a new topic of discussion each Thursday, outlines the research of a scientist named Hristo Bojinov. If my oddly advertiser-like opening sentence of this paragraph (I swear I'm not getting paid) was a tad convoluted, the story of this week's Nautilus postings is "Safecracking the Brain." The process by which Bojinov began his research was to think of how to design security measures that use the brain's modus operandi as the basis for stronger security measures.
"Rubber hose attacks," described in the article as, for example, a "thief taking someone at gunpoint to an ATM to withdraw money," capitalize on explicit memory, things which we consciously know, thus subjecting us to external pressures. Bijinov's alternative is to use our implicit memory, e.g. Riding a bike, playing a video game, writing this blog post (No, not really) to combat against rubber hose attacks on the Web. How? Well, in an awesomely relevant way, Bijinov designed a "game" to help get this research done. It is a two-part experience, an hour for each, which utilizes falling circles corresponding to the S, D, F, J, K, L keys a la Guitar Hero.
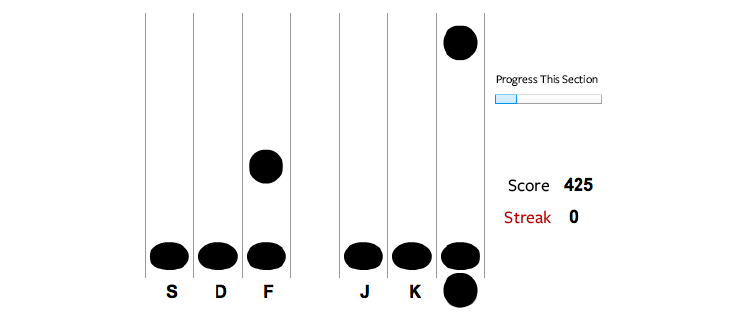 |
| "Through the Fire and the Flames" -- Crypto Version. |
Repeating a certain sequence for each hour, Bijinov believes, and has evidence*, that the repeated sequence in the context of a game will embed the lengthy (near 30 letters) password in our brain so that when entering it on some website it is second nature.
Of course, Bijinov used Amazon's Mechanical Turk service to get some results, and after having his participants play the game for 60 minutes at one time and the same game (either with the same or different sequence) 24 hours later, he found that the players who encountered the same sequence were 5-10 percent better than those who had new sequences*. A fascinating potential corollary to this is that a game like this, albeit much, much shorter, be used when logging into a website. With this in place, an authenticator could detect a hacking attempt by comparing the users' speeds.
Bijinov has some interested researchers looking to implement it, but it's a long way before it would be used commercially.
Look, I understand this is definitely one of those cool-but-probably-not-feasible-in-the-real-world findings, but the logic is there. I personally don't feel that this could be used on a Web-wide scale, but the idea of embedding our security passcodes, -words, and -phrases into our brains to ensure maximum security is one that can certainly be utilized on an individual, per-person basis. Heck, you can all try it now, working on embedding the lengthy, otherwise unmemorable password at a subconscious level and tightening your personal cryptography.
Oh, and it pays 10 bucks. I actually might do this. It's not for the money, I swear.
I remember reading an article about this a couple months ago. While it sounded cool, taking an hour out or my day to log into facebook seems a bit ridiculous. The article I read took time to illustrate that this type of security would be most useful as an extra security layer around highly sensitive data. An hour might be a bit much for facebook but not for accessing all the phone records that NSA has collect. It might even deter people from using the data incorrectly. (People are lazy)
ReplyDelete